Don't wait for a breach to take action
Cyber threats don't wait - and neither should you. Let's secure your business with a solution tailored to your needs. Reach out to us today to get started!

Protect your business from advanced threats with cutting-edge security features, incl. EDR, anti-ransomware, and AI-powered defenses.

Ensure your critical data is always safe with real-time backups and automatic recovery, minimising downtime and data loss at affordable rates.

Get enterprise-grade cybersecurity and data protection without breaking the bank, offering unbeatable value for comprehensive coverage.
Advanced cyber protection for every endpoint in any location - making it ideal for today's mobile and remote work environments - with native integrated backup and endpoint management. Advanced attacks can only be countered with advanced security.

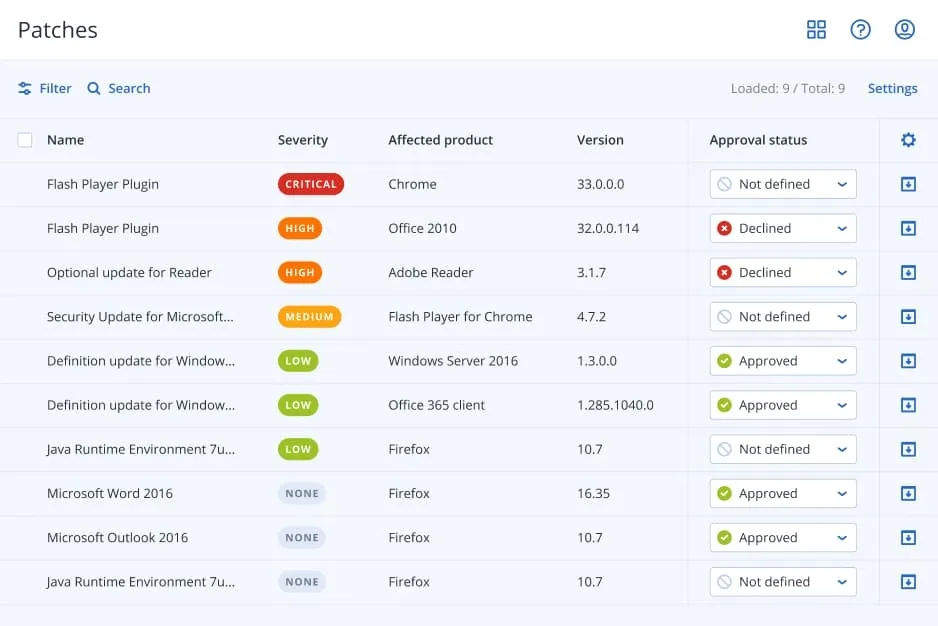
Vulnerability assessments, patch management, security posture monitoring, threat hunting, removal of malware from backups and automatic protection of new devices.

Continuous data protection, real-time threat protection, and informed threat investigations and ML-based monitoring of workloads to detect issues before they cause downtime.

Rapid response to security incidents and recovery of data with attack rollbacks. integrated disaster recovery and additional investigation capabilities like forensic backups and secure remote desktop access.
Award-winning endpoint protection trusted by
Try our cybersecurity service obligation-free for 30-days.
By submitting this request you automatically agree to our Privacy Policy.
In the face of increasing attack sophistication, volume and pace — driven by AI — organizations require a complete security framework to identify, protect, detect, respond and recover. The synergy - native integration of cybersecurity, data protection and endpoint management - allows you to protect your systems while keeping costs down.
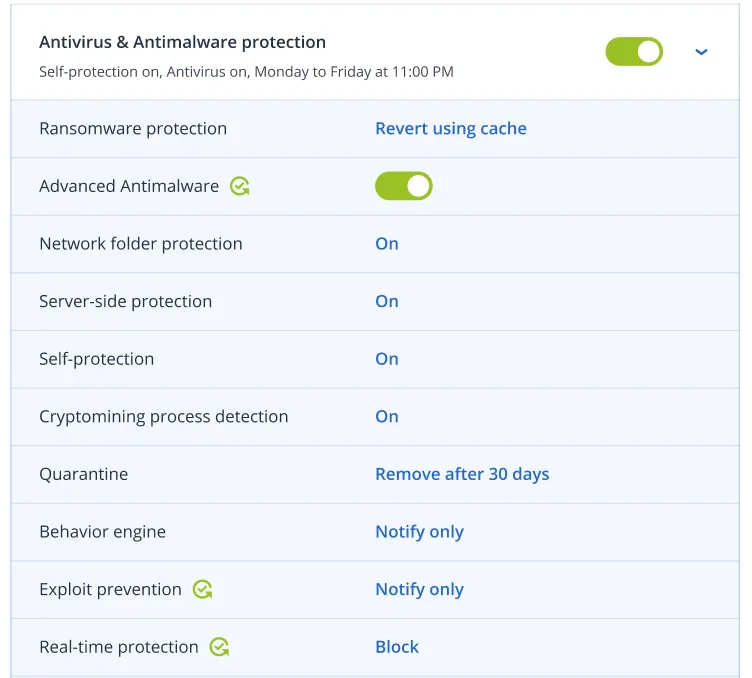
Replace inefficient, legacy antivirus with integrated cyber protection that includes full-stack anti-malware. Increase your detection rate and responsiveness to the latest cyberthreats. Extend cyber protection to web browsing, backed-up data, the recovery process and exploit prevention.
From automated patching to remote monitoring, we streamline your operations, reduce risks, and ensure all your devices are secure and up-to-date; no matter the size of your business.
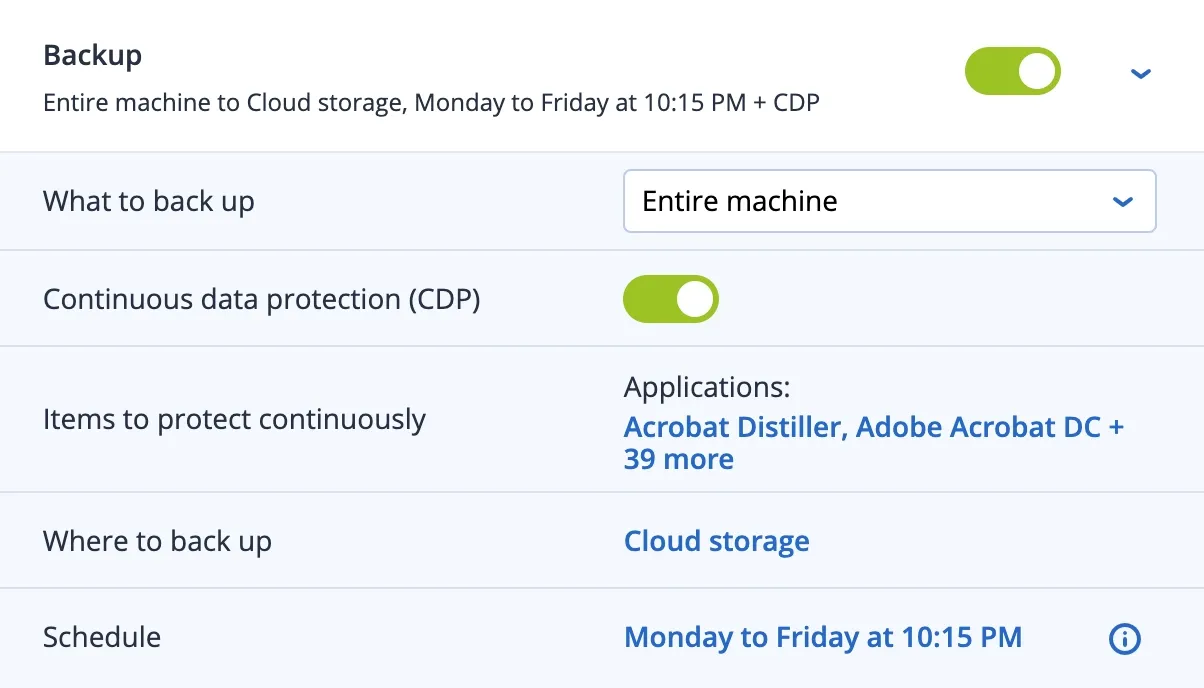
Overcoming increasing IT infrastructure complexity and cyberattack sophistication requires a comprehensive backup solution to keep every bit of data safe. Our solution integrates backup with advanced anti-ransomware technologies to keep your data safe from any threat.

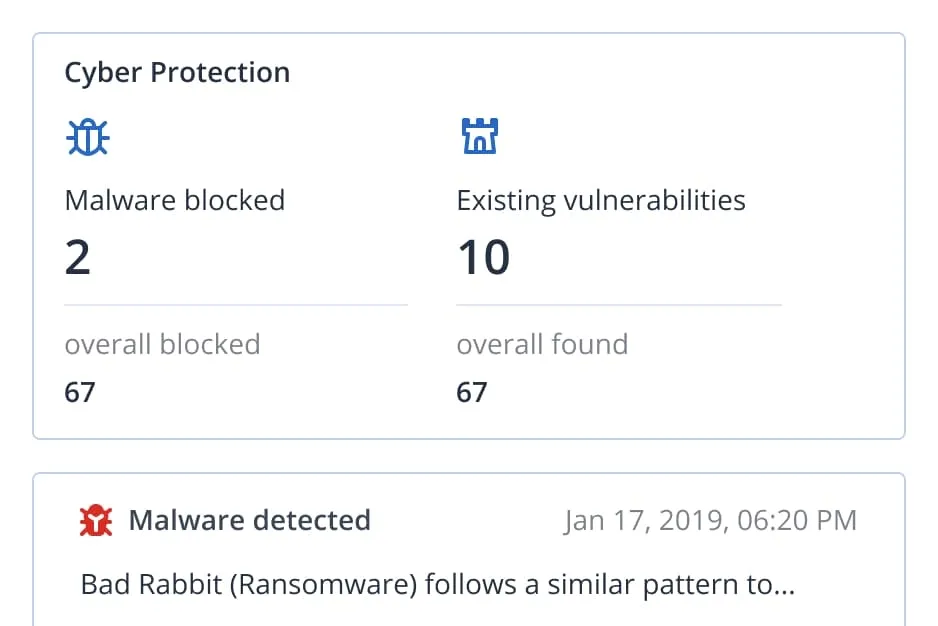
Cyber Protection Operation Centers (CPOC) continuously monitor the cybersecurity landscape and release real-time alerts on potential threats including malware, vulnerabilities, natural disasters and other global events.

Identify and remediate vulnerabilities in your system. with machine scanning to ensure all applications and operating systems are up-to-dates.

Stop and prevent attacks from happening with memory protection, return-oriented programming protection, code injection protection and privilege escalation protection.

Proactively protect collaboration tools with vulnerability assessments, patch management, code injection prevention and anti-malware capabilities.
Automating threat detection and response to keep pace with evolving threats.












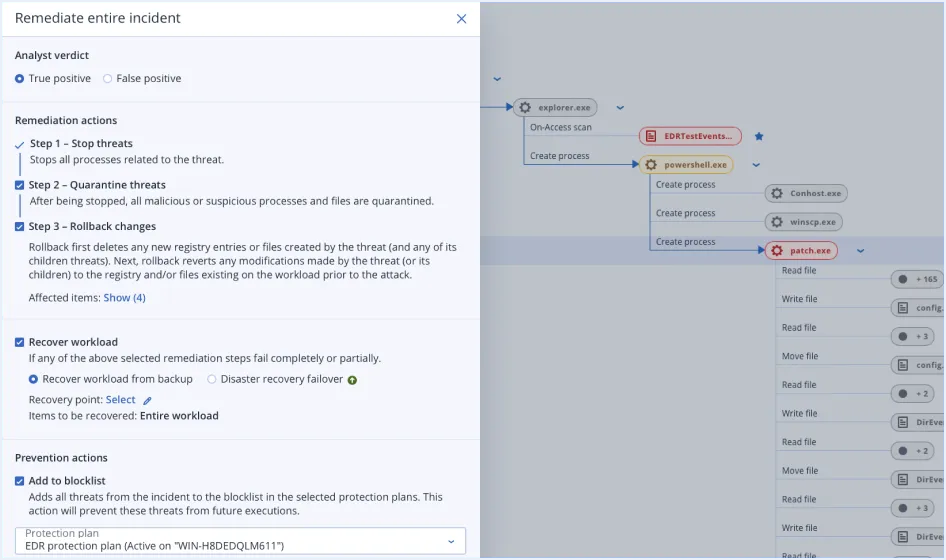
Prevail where point solutions fail - leverage the full power of integration among cybersecurity, data protection, and endpoint security configuration management via a single-click response to incidents.
Quickly and easily roll back attack damage, including affected files, data and configurations - streamlining remediation without depending on the vulnerable Microsoft Volume Shadow Copy Service that most solutions leverage.
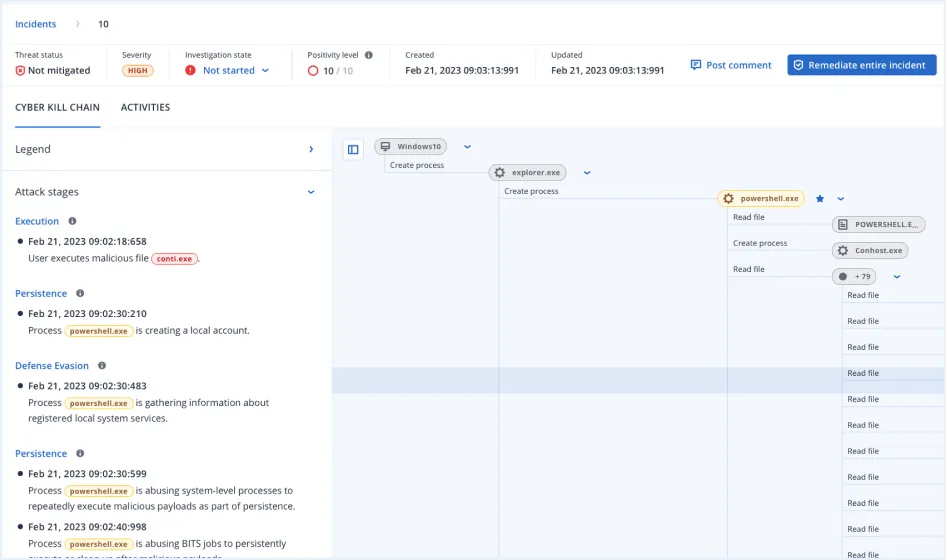
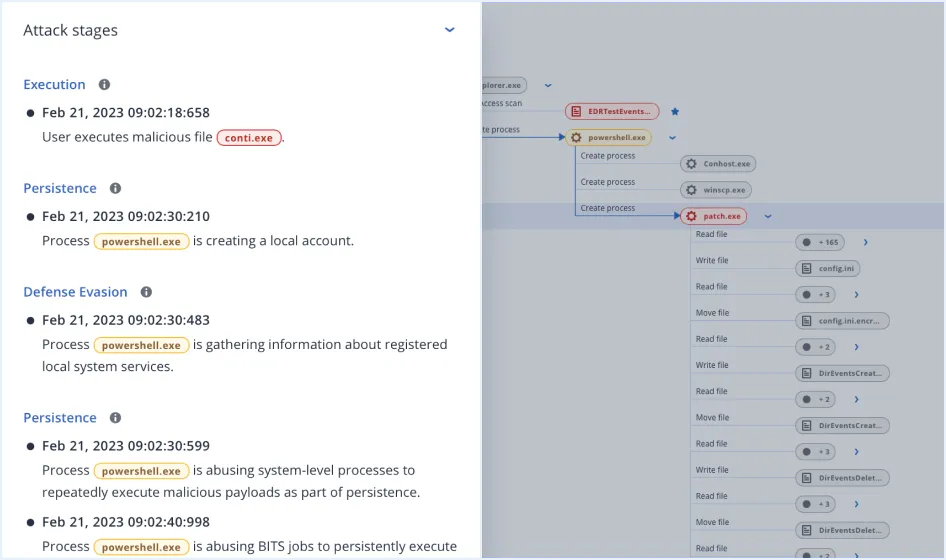
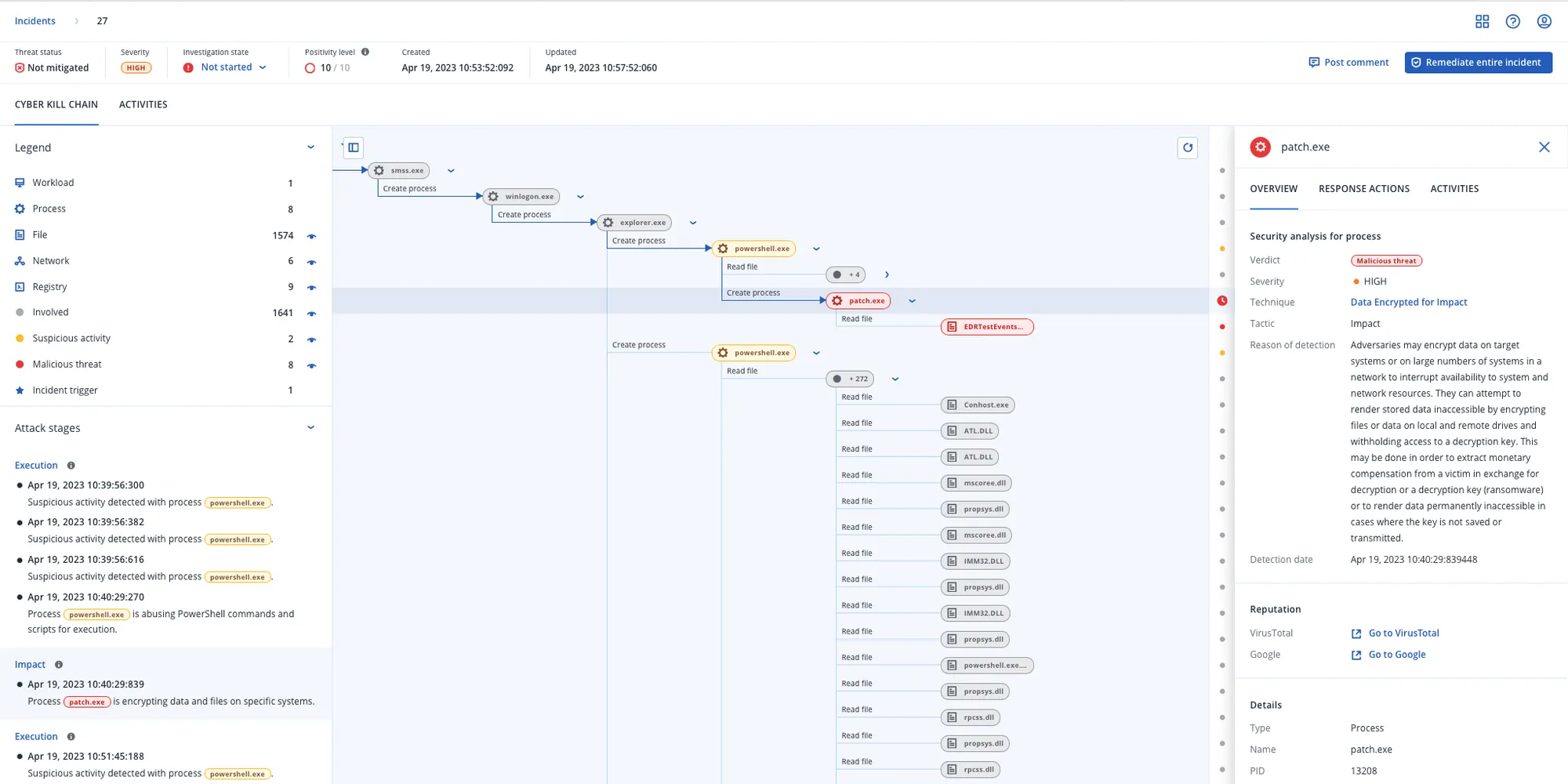
Streamline response and increase reactiveness to threats, leveraging AI-based interpretations of attacks mapped to MITRE ATT&CK® to understand in minutes:
Streamline incident analyses and response times even further by benefiting from AI-generated summaries that provide a brief overview of each incident.
Focus on what matters and increase your responsiveness to attacks by leveraging automatic incident alerts that are prioritised based on criticality, so your team can focus on remediating instead of hunting.
Remediate attacks by stopping malicious processes and quarantining analysed threats - blocking them from execution as aprt of unified, single-click response capabilities.
Stop attacks from spreading and effecting more endpoints - you can isolate affected points from the network to prevent lateral movement.
The solution monitors events on an endpoint level and automatically correlates them in attack chain graphs per incident for easy analysis.
Prevent business-critical data from getting into the wrong hands by remotely wiping compromised or missing Windows devices. You can protect data from being deleted by disgruntled employees or accessed from lost or stolen devices.
Data loss can strike when you least expect it - whether from hardware failure, accidental deletion, or ransomware. In fact, studies
show that over 60% of businesses only implement proper backup and recovery strategies
after experiencing a major data loss event.
With our integrated backup and recovery solution, you don't have to wait for a crisis. Our solution ensures your systems
and data are continuously protected and easily recoverable, giving you the resilience to bounce back without missing a beat.

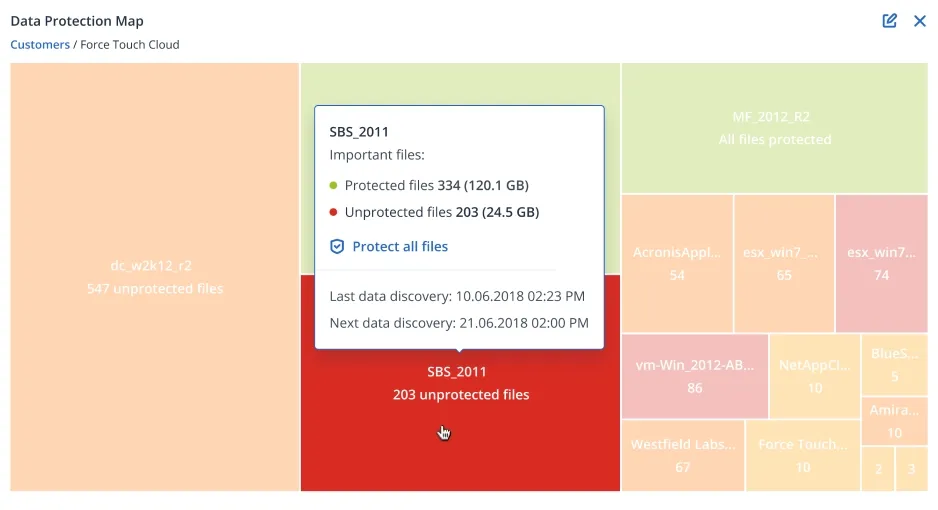
Ensure that critical data is protected for compliance reporting with the data protection map. Use the automatic data classification to track the protection status of important files and alert admins if sensitive client data is not being backed up.

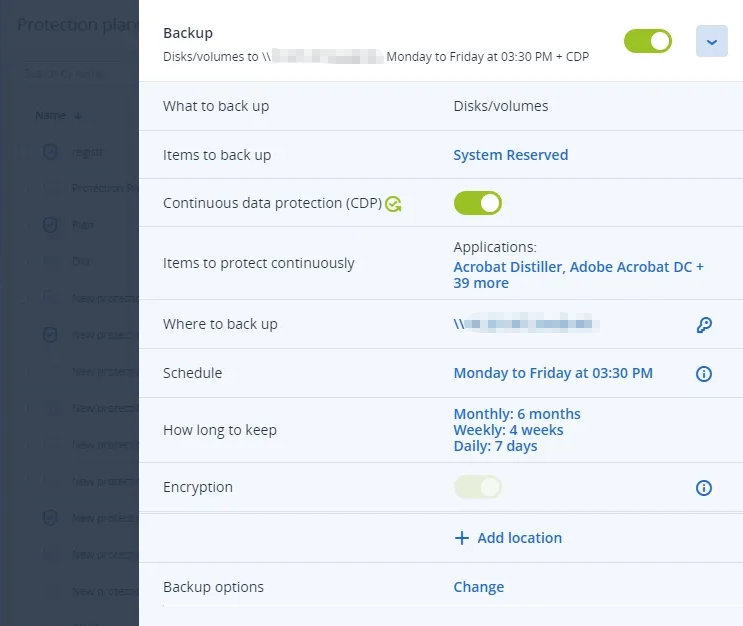
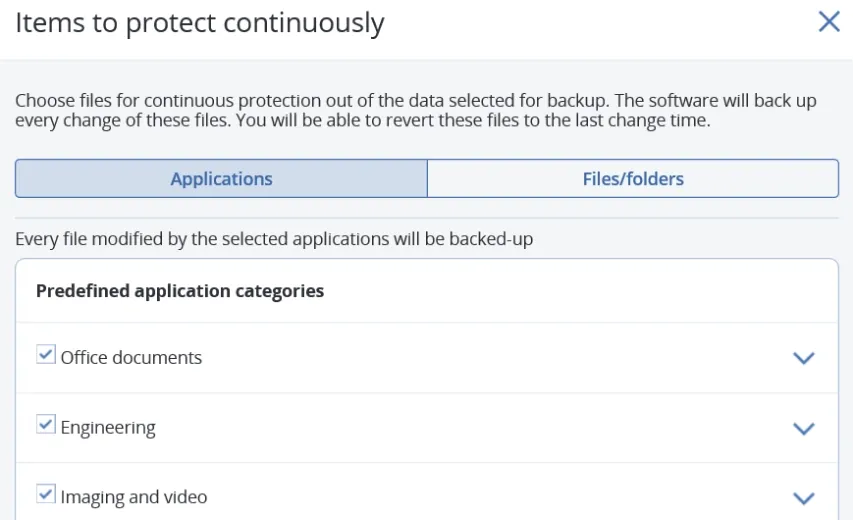
Ensure users don't lose the work that is in-progress by defining a list of critical apps that they frequently use. The Agent monitors every change made in the listed applications and continuously backs them up between scheduled backups so no data is lost.






During the backup of the entire workload, metadata is collected for each database. You can browse databases and/or fully or granularly recover data and tables without recovering the entire workload.
East IT administrative burden with built-in capabilities for easy backup and recovery of Microsoft Exchange, Microsoft SQL Server, and Oracle DBMS Real Application clusters.
Strengthen your SAP HANA database protection with consistent, script-based, disk-level backups that simplify management and do not require any SAP HANA expertise.
Cyber threats don't wait - and neither should you. Let's secure your business with a solution tailored to your needs. Reach out to us today to get started!